Finance professionals interact with Windows security every day when they provide a username and password to login to their computer/network. Another common interaction occurs when they want to install a new application and are stopped and forced to call IT. Finance professionals can struggle when security prevents them from accomplishing necessary tasks. As we have argued elsewhere, it is useful to have a bit of insight into how Information Technology works so you can either:
- solve the problem yourself or
- better communicate with IT.
Just as we did with passwords, we also hope to provide finance professionals in small organizations with a better perspective on how their IT department (often outsourced to consultants) ought to leverage File Access Permissions to help mitigate risk.
There are many different kinds of security involved on a typical computer helping protect you or your organization from problems (malware infecting your network, unauthorized access to company files, etc.). One such security mechanism is called File Access Permissions. Please note that this topic is actually complex and varies by specific operating system. Thus to keep it brief we will simplify some topics (while being largely accurate) and assume a recent Windows operating system.
Access Control Lists and Permissions
Each file, folder, and network share have an associated Access Control List (ACL). An ACL is a list of users/groups that have specified access rights to the file/folder/share dictating what they can do with it (called Permissions). Common permissions include Read and Write.
ACL entries might look like this:
File: Inventory2017.xlsx
User Bob: read permission
User Mary: read/write permission
Assuming no other rights are granted elsewhere, user Bob has permissions to read the file, but only user Mary is allowed to both read the file and make changes to it. If user Bob tries to save the file, he will get an error.
In a well-designed network, ACLs are usually defined a bit differently as the above example is quite brittle and hard to maintain. If you had to assign access rights file by file imagine how much work this would be and how easy it would be to make a mistake.
Active Directory, Security Groups, Files and Folders
In a typical Windows-based network, information on all employees, consultants, and computers are stored in a central directory called Active Directory (AD). As you can see from the image below, it is nothing mysterious. It is a hierarchical tree (like an organizational chart) grouping users and storing details such as your login name, password, email address, etc.
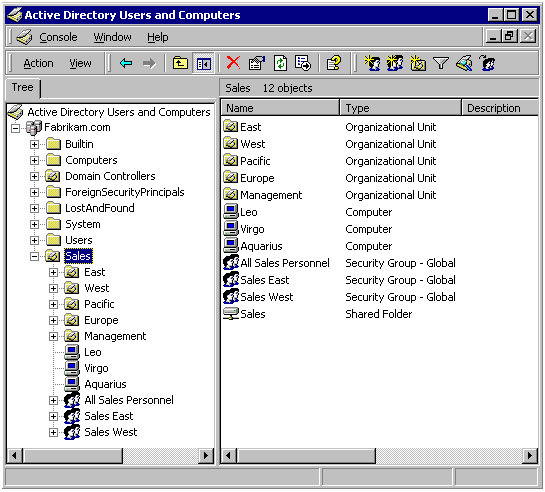
The grouping feature is valuable. The idea is simple - a security group is a collection of people that share similar access rights. For instance, HR staff may need access to specific files while Accounting may need access to different files. By creating an HR group and an Accounting group, and adding all HR staff to the HR group and Accounting staff to their group, the IT administrator can now apply security policies based on groups, and not individual users. When an HR employee leaves the company, and a new one is hired, the employee only need be added to the right group and all access permissions will automatically apply to this user.
Thus, a well-designed ACL list will leverage these groups and might look like this:
Folder: E:\data\human resources
Group HR Staff: read permissions
Group HR Managers: read/write permissions
Two benefits of the above approach:
- The ACL is applied to the whole folder, ensuring that all files and folders stored in that folder have the same permissions. New files will automatically share the same permissions as the folder.
- Permissions are assigned to groups. Thus anyone belonging to the HR Staff group to have read-only access to the files and folders, and HR Management to have full access. This reduces the workload on IT and ensures consistency.
Network Shares and Conflicting Rights
In addition to file and folder level ACL entries, a network share can have a separate set of permissions. In the example above, assume the location is shared on the network under the name "human resources", then the share itself can have an ACL associated with it similar to the following:
Share: \\server\data\human resources
Group Everyone: read
If the ACL on the share were configured as above, nobody would be able to write to that folder. Both the share and the file/folder based ACL need to allow access. They are defined in two different locations and are not related to each other in any way. The best way to think of this is the most restrictive permission set wins.
One other permission that you should know of besides Read, and Write is Execute. A program file requires you to have the Execute permission before you may launch it.
Attributes
Lastly, files and folders may have certain attributes.
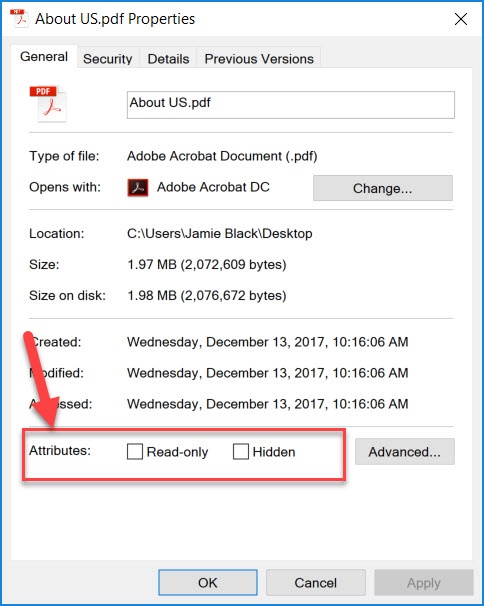
The Read Only attribute is significant to end users as this flag may override any write permissions set on the file. If a file is marked as Read Only, the user will be unable to modify it even if they have the write permission in the ACL and the shared folder permissions that we discussed above. This flag can usually be removed by the end user as long as the user has write access to the file. Once the flag has been removed, the file can be written to assuming the user has write access based on the ACL set.
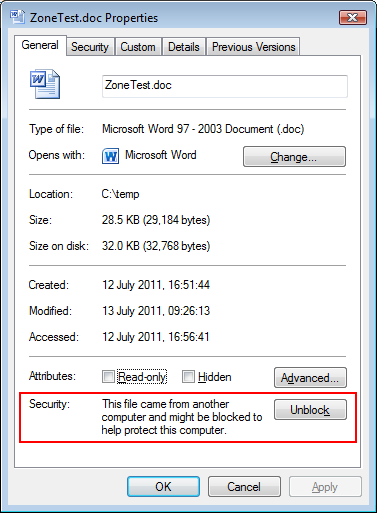
Security Warnings on Downloaded Files
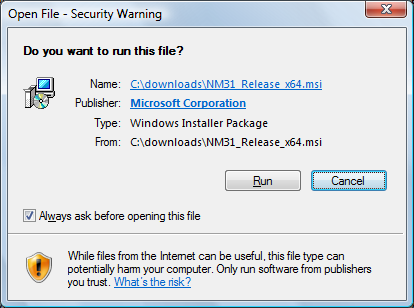
One last issue you may run in to from time to time has to do with files downloaded from the internet. If you are using Windows 7 or later, your computer keeps track of the source of the file and will protect you from files that originated outside of your organization. Windows uses a feature called "Alternative Data Streams" (ADS) to remember which files originated from external network sources. When Windows detects you trying to open one of these files, it will warn you. If your IT department allows you, Windows will ask for your explicit permission to open it. However, your IT department can set up your permissions so that you do not have any choice and are simply blocked from opening these file
In conclusion, then - accessing files and folders in Windows is broken down into several layers of protection:
1. File/Folder based ACL assigned to Groups/Users
2. Network Share-based ACL assigned to Groups/Users
3. File-based Attributes such as Read Only
4. Downloaded file based ADS blocking access
All four layers need to grant you access before you can work with a file. Also, access might be partial such as read-only or read/write only but not delete.
What you should try if you have access issues:
To check whether you have access to a file or folder, open File Explorer and navigate to the file/folder in question, right click and select Properties.
1. For file-based ACL rights, go to the Security tab. Click on your name or the AD group you belong to (you may need to ask IT if you do not know this) and check your permissions.
2. For network share-based ACL, locate the mapped network drive, right-click the drive and select Properties. The Security tab will show the ACL for the network share.
3. For file-based Attributes, review the General tab and check if Read-only is ticked.
4. To see if a downloaded file is being blocked (assuming you have write access to the file) right click it, select Properties and then unblock it at the bottom of the Properties window.