Working from home, especially for the first time, may seem a bit like leaving home as a young adult. You enter a brave new world, free of the protections your parents' home provided to discover yourself. In this case, the office is the secure home you are leaving, at least from an IT security perspective.
One of the security issues to consider when working remotely is phishing. This article defines the problem, provides a real-world example and eight steps to avoid phishing attempts.
Phishing
The definition of a phishing attack:
A fraudulent attempt by an adversary posing as a legitimate entity to steal sensitive information from someone.
The problem
Chances are you have seen emails from someone familiar asking you to click on a link or download an attached file. With some review, you realized the person who sent it is not the person they claimed to be. The idea behind this attack is to gain your trust by posing as someone you know. The basic process is shown below:
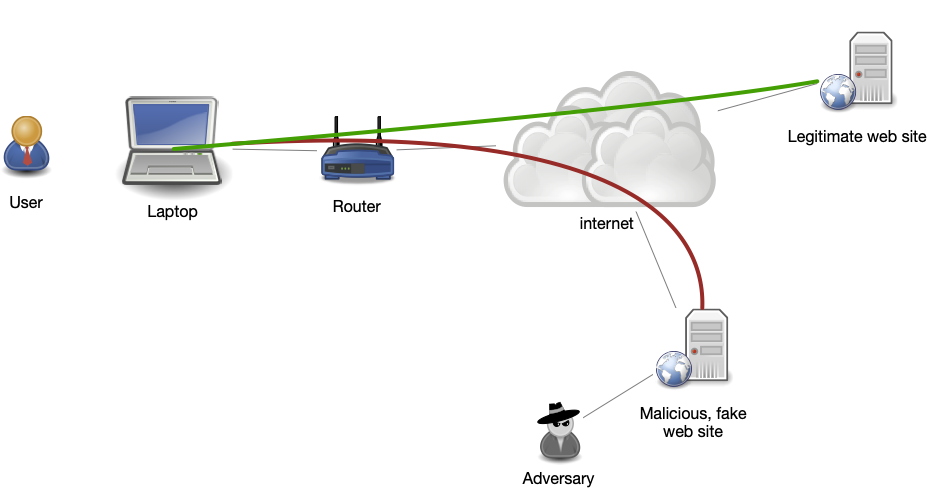
The adversary's phishing email causes the user to connect to the malicious site (red connection) controlled by the adversary, instead of the legitimate web site (green connection). This allows the adversary to intercept the login credentials of the user.
Below is a real-world scenario that we will be analyzing. All the suspicious elements visible to a non-technical user have been highlighted in green. It purports to be from our phone system, informing me that I have a new voicemail. We analyze it below.
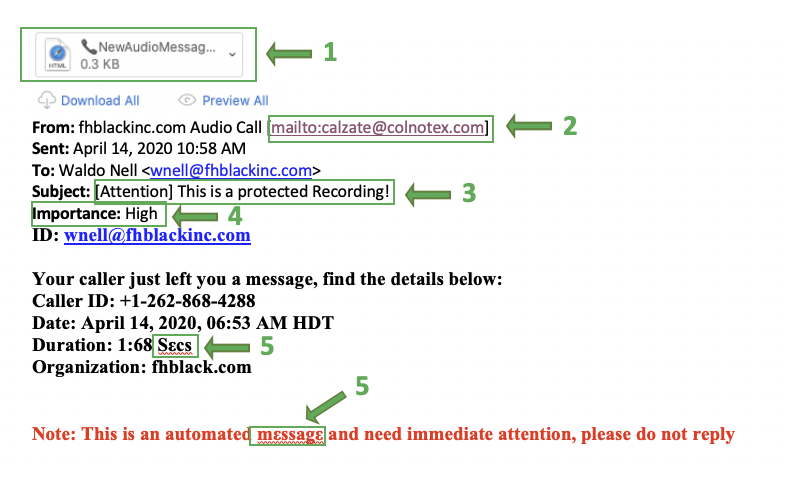
- The email has a file attached. Carefully reviewing that attachment shows it to be an HTML file. If this were a real voicemail attachment, it would be a WAV or Mp3 file.
Another approach, not used in this message, includes a link the user is asked to click to perform some action. This link might look like the one below: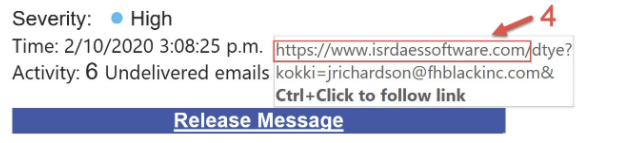 If the user hovers their mouse cursor over the link "Release Message", the actual URL that would be opened is displayed (as highlighted above). Often it is clear that this URL points to a domain that is not related to the sender of the email.
If the user hovers their mouse cursor over the link "Release Message", the actual URL that would be opened is displayed (as highlighted above). Often it is clear that this URL points to a domain that is not related to the sender of the email. - The FROM address is not from any known domain and does not match the name of the sender.
- The subject is suspicious. What does a "protected recording" mean?
- Misuse of the Importance flag. Identifying an email as High Importance is a common tactic among phishing attacks.
- Font substitution is also a common technique used to try and bypass spam filters. It works by randomizing some letters to look like valid English letters. Since the Greek ε is not the same as the Latin e, it could fool anti-spam algorithms.
What happens if the user doesn't notice any of the above warning signs? In this example, the following occurs:
- If the user double clicks on the attachment named _NewAudioMessageFile_000.htm. their browser loads the contents of that HTML file locally.
- A page is loaded that redirects to a new website (owned by Mary Jean Suarez in the Philippines) that looks like this:
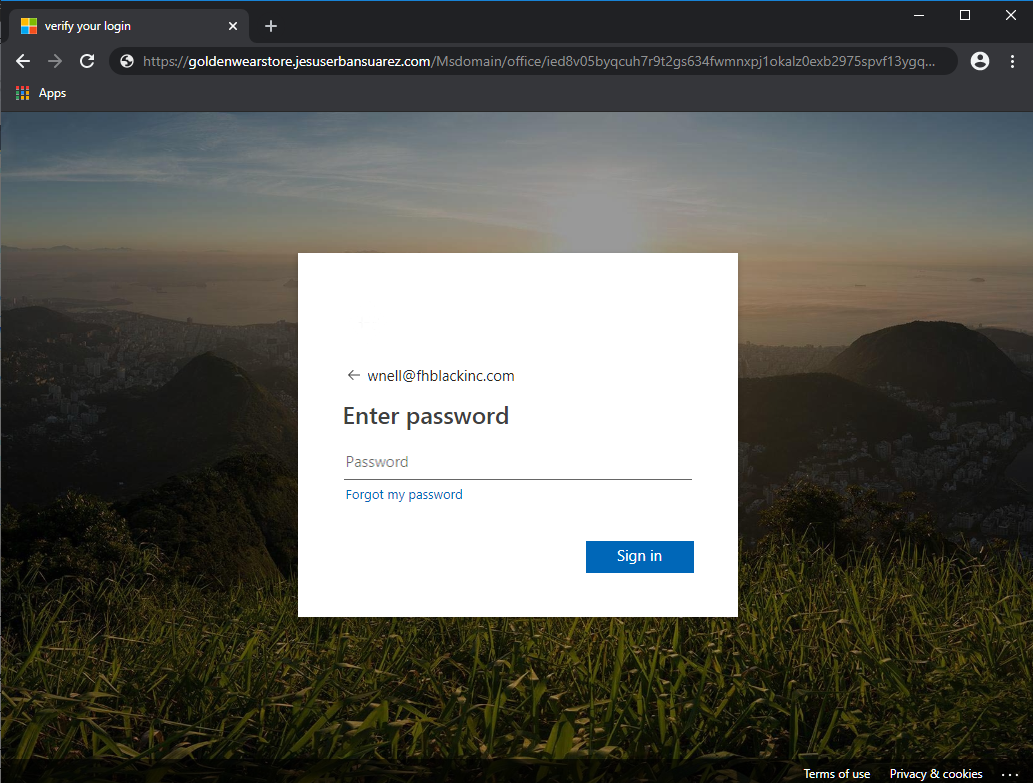
Note this is not a Microsoft URL but was made to looks like a Microsoft page to appear even more legitimate. - If the user stops here, the adversary knows the email address that received the email is active and that the link was clicked. No compromise of any account has occurred yet.
- If the user enters their password (correct or incorrect) and clicks Sign In, the password, together with the email address, is sent to the adversary's server (called credential harvesting). The following page is displayed:
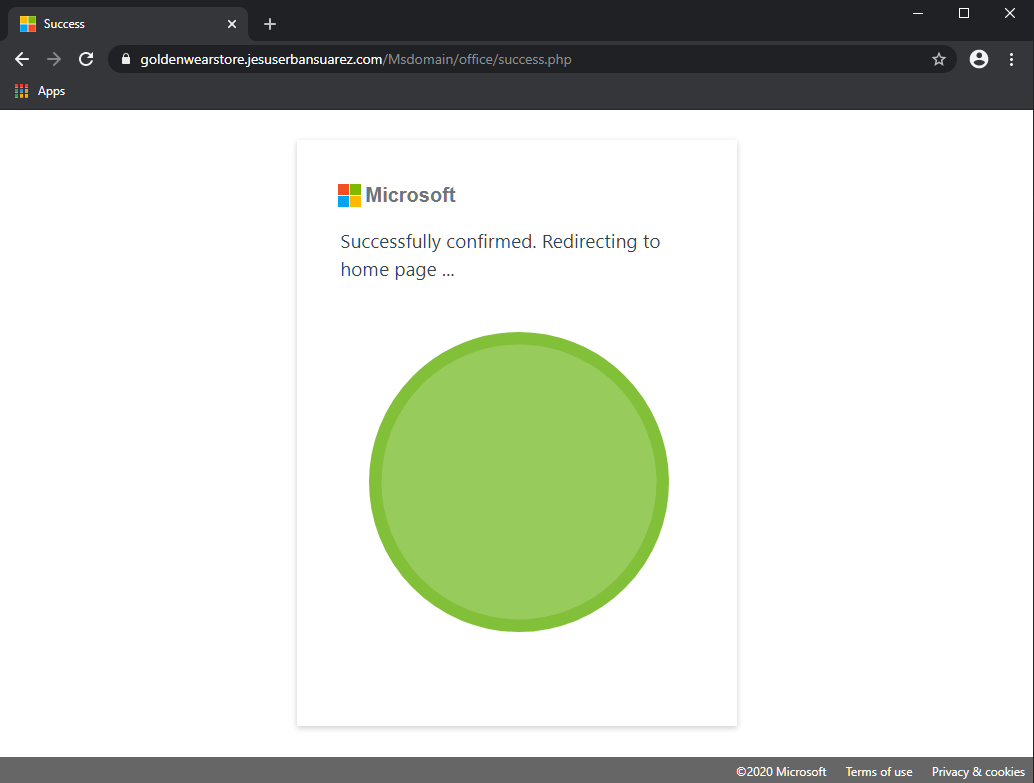
- As the adversary does not know if the supplied password is valid or not, the best they can do is to forward the user to the real portal. The page then redirects to this legitimate Microsoft web page:
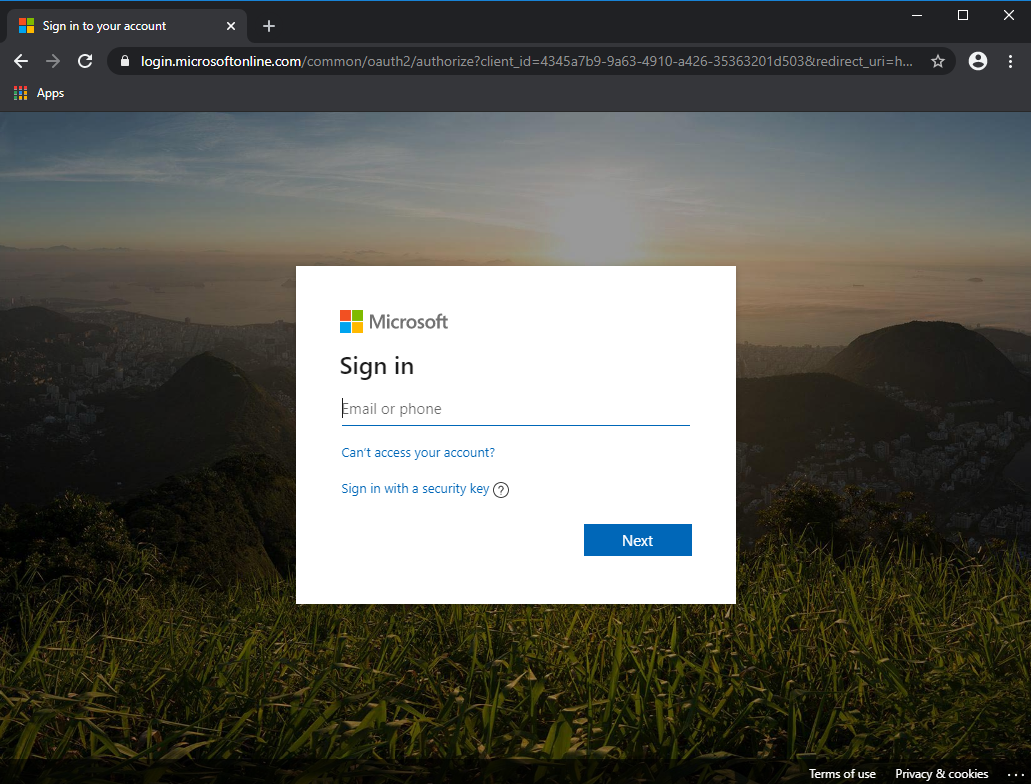
Most users would not think twice about having to log in again, assuming perhaps they mistyped something. This time, the user is logging in to the real Microsoft web site. The scam is completed.
If the user entered their correct password in step 4 above, their account has been compromised, and the adversary now has full access to the account. You should immediately change your password and monitor your account for suspicious activity.
The mitigation
Phishing attacks are nothing new. But they have increased 350% during the pandemic and are now more dangerous than ever because:
- Your computer is no longer offered all the protections of the office network,
- You have no direct access to IT to question suspicious emails/activities,
- If you are using your home computer, it is likely un-patched, making it easier for phishing attempts to work successfully,
- Because we are working in unprecedented times and are likely working remotely, requests that would have stood out as unusual two months ago might slip by unnoticed today.
What can you do to protect yourselves? Below are eight recommended steps to take to increase your protection:
- Realize that it is inevitable that you will receive many phishing attempts, and you have a responsibility to be vigilant.
- Know how to spot a phishing attempt. This can be very complex and technical; however, there are several markers you can watch out for to identify most phishing attempts:
- Email FROM addresses can be easily faked. Just like in our example above, phishing attempts will get the name in the FROM field of an email to reflect someone you know but not the email address. This is not universally true, but it is a good first warning sign.
- If the email asks you to click on a link, pause for 10 seconds, and carefully consider whether the email was expected. If not, contact your IT department to verify the validity before clicking any links.
- An additional safety measure you can take is to hover your mouse over the link in the email. Make sure the domain in the link (i.e. the site it is pointing to) seems familiar.
- If the email asks you to perform any sensitive operations like releasing payment etc., it is best to call the sender via a known number and verify the request.
- Disable automatic loading of images. Most email applications allow you to turn off automatic loading of images in emails. This is recommended as many phishing attempts work by including a link to an image that lets the attacker know your email is legitimate.
- Another useful trick is not to click the link given in the email, but rather open a new browser window and go to the site in question yourself. For instance, if you get an email about a Microsoft Office 365 account needing updated payment details, don't click the link in the email. Instead, open a new browser window and type in https://portal.office.com and go to the billing section yourself. This will thwart the phishing attempt. Sometimes this is not possible, such as when the email contains a link to a file you need to view.
- Enable Two Factor Authentication (2FA) on all critical systems. If this was enabled in our example above, the adversary would only have your password but would be unable to log in.
- Be sure your computer is set to download and apply patches automatically. Applications are often adding features to detect and warn users about suspect emails automatically.
- Finally, never allow someone to connect remotely to your computer unless you know them.
While there is no single thing you can do to prevent a phishing attempt from succeeding, these basic guidelines can greatly mitigate the risk of falling prey to a phishing attempt.
© 2025 FH Black Inc. All rights reserved. Content may not be reproduced, excerpted, distributed, or transmitted without prior written consent.



